IGEL announced the successful conclusion of a joint effort with Asc3nd Technologies Group (ATG), Cisco, and the National Defense University (NDU)[1], implementing a repeatable, standards-based architecture that enables rapid Comply-to-Connect (C2C) and Zero Trust compliance for the U.S. Department of War (DoW).
The initiative demonstrates how existing endpoint hardware can be securely repurposed to meet strict DoW network access controls, reduce operational complexity, and accelerate time-to-compliance in mission-critical environments.
Mission Assurance Through Endpoint Control
Working with NDU, the team implemented a controlled, policy-driven device program designed to pass rigorous DoW C2C posture checks, enforce workload segregation, and integrate Zero Trust policy enforcement at the endpoint.
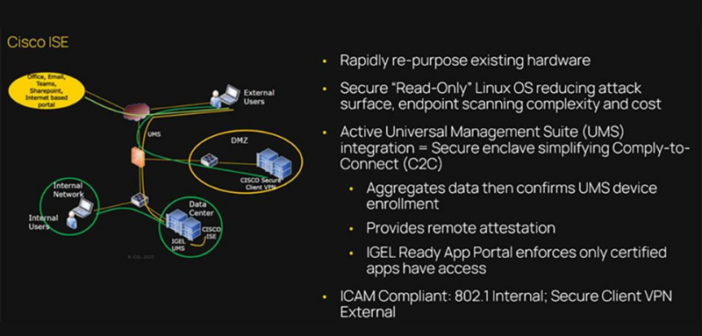
Cisco Identity Services Engine (ISE) served as the policy decision point, delivering identity validation, posture validation, and continuous monitoring endpoint compliance. IGEL’s immutable, read-only endpoint OS — centrally orchestrated by the Universal Management Suite (UMS) — provided the trusted endpoint architecture that minimized the attack surface, enforced configuration integrity, and eliminated local data storage.Together, ISE and UMS created an end-to-end trust chain — where UMS ensured endpoint compliance and ISE continuously verified it before granting or maintaining network access to the endpoint.Through standards-based API integration, Cisco ISE pxGrid Direct integration dynamically queried UMS for enrollment, configuration, and real-time compliance status. Once requirements were met, ISE automatically applied network policies — including segmentation, Security Group Tagging (SGT), and VLAN assignments, granting mission-ready access to compliant devices and restricting non-compliant ones to limited access until remediated.
- Immutable Endpoint Security: The IGEL Preventative Security Model™ ensures no local data through a modular OS and tamper-proof configuration
- Continuous Posture Validation: Automated compliance checks are completed before and during network access
- Policy-Driven Automation: Network segmentation and authorization are achieved without manual intervention
Beyond the initial deployment, the architecture is adaptable to multiple DoW and public sector missions – from VDI/DaaS to enterprise browsers and fit-for-purpose operational workspaces, enabling secure, efficient endpoint operations across diverse environments.
Partnership Perspectives
“Comply-to-Connect is the tactical on-ramp to Zero Trust,” said Sarn Bien-Aime, CEO of Asc3nd. “By grounding this project in open standards and automation, we’ve demonstrated how agencies can accelerate mission outcomes while staying within constrained budgets. Our collaboration with NDU proves that Zero Trust can be delivered in production quickly, securely, and without slowing the mission.”
“Prevention at the endpoint, combined with centralized orchestration through IGEL UMS, reduces risk, simplifies compliance, and accelerates time-to-mission,” said John Walsh, Field CTO for Critical Sectors, IGEL. “That’s exactly what our public sector customers are demanding.”
To learn more about how the DoW is advancing Comply-to-Connect and Zero Trust readiness, click here to read the full IGEL blog.
Related News:
IGEL and Carahsoft Partner to Expand Public Sector Secure Endpoint Access
IGEL Acquires Stratodesk, Expands Adaptive Secure Desktop
[1] Prior to the federal government shutdown on October 1st, 2025.