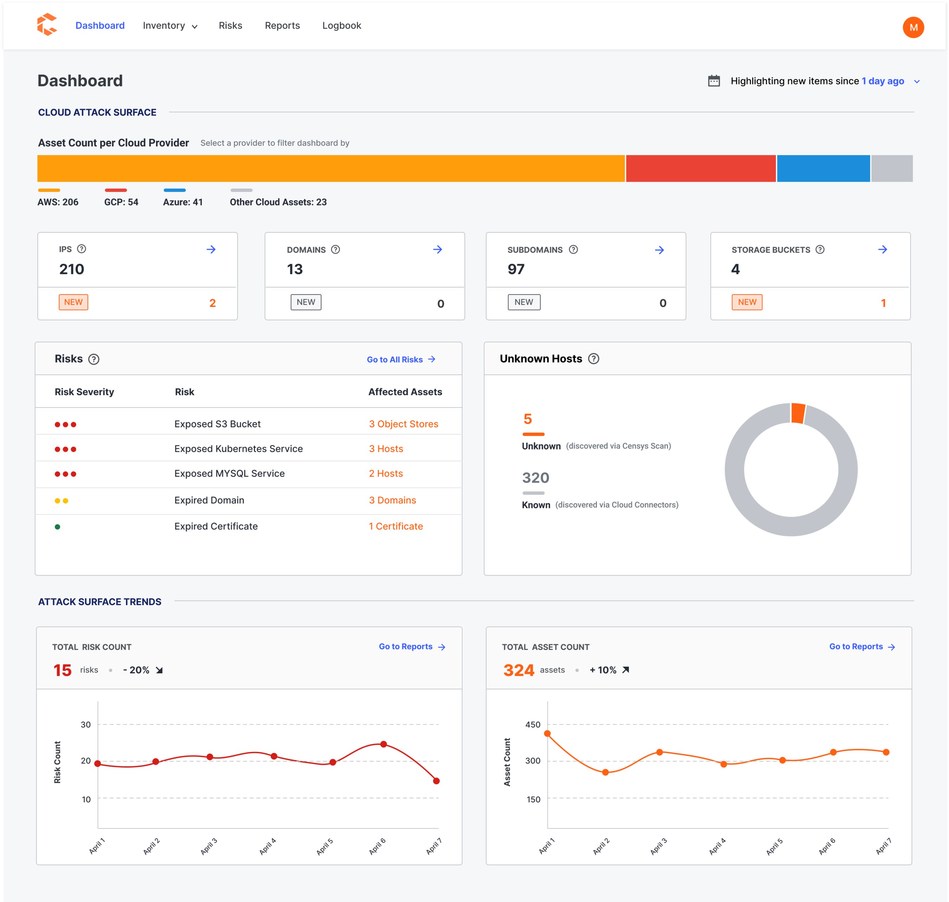
Censys, announced a new Cloud Security Offering, including cloud storage bucket discovery and risk analysis, daily asset scanning, and a centralized and complete cloud inventory across all your cloud providers as part of the Censys Attack Surface Management Platform security offering.
Data breaches have become an increasingly commonplace incident in the modern enterprise, and the role of the cloud in its growing prevalence is undeniable.
“We recently analyzed our own Universal Internet DataSet and found 2 million database exposures across the most common cloud providers, as well as 1.9 million RDP exposures,” said Censys’ Security Research Lead, Megan DeBlois. “We know that database exposures lead to data breaches, and past research has shown that RDP accounts for 70-80% of network breaches.”
Increasing concern from customers and our internal research pushed Censys to address the underlying lack of cloud visibility that is causing these risks. Many of our customers used CSPM, CASB, and CWPP platforms, but these only monitor known cloud accounts. Customers can now continually discover cloud assets and risks ranging from unknown cloud accounts and providers to unmanaged cloud storage buckets, thereby eliminating security blindspots and resolving some of the Internet’s most alarming risks.
Daily Discovery of Cloud Providers, Accounts, and Cloud Storage Buckets at Scale
Censys Cloud Security is a big step toward addressing modern security concerns. Censys now harnesses its industry-leading asset discovery capabilities in combination with cloud provider integrations such as AWS, Azure, GCP to ensure multi-cloud visibility. Censys combines data obtained from these methods to provide a single unified asset inventory containing both known and potentially unknown Internet-facing cloud assets. Unlike competitors, Censys also addresses the ephemeral nature of cloud assets with twice daily scans of the top 100 IPv4 ports.
“Most Fortune 500 companies have hundreds of cloud accounts. While some are managed through cloud security tools, many are simultaneously created by non-IT groups and don’t have technical controls to prevent a breach,” said Censys Co-Founder Zakir Durumeric. “Security teams are left with a huge environment to protect, but are blind to many of their riskiest accounts.”
Unmanaged cloud accounts can contain an organization’s riskiest assets. “One of our customers thought they had just 800 hosts in their attack surface, but after connecting their AWS accounts to Censys Cloud Security, we inventoried a total of 1,439 – nearly an 80% increase. This discovery revealed 60 exposed protocols and end-of-life software risks on otherwise unknown assets,” said Durumeric. “In order to maintain compliance and avoid security breaches, it is imperative to have comprehensive and continual cloud asset discovery for all assets regardless of the cloud account or provider.”
In addition, discovery of new cloud asset types such as storage buckets have provided immediate value to customers. “A significant problem that remains is dealing with data loss from misconfigured databases and buckets, which has resulted in numerous data loss events over the years,” said Derek Abdine, CTO at Censys. “Censys has added storage bucket discovery after overwhelming demand from customers. After switching on the feature with one customer, we found 18 exposed buckets, one with a completely configurable access control list. That means anyone on the Internet could have changed the settings and accessed the data.”
Using Censys Cloud Security, teams can finally get full visibility of their cloud footprint across all providers and deployment models, reduce their attackable surface area by shutting down shadow IT, and meet compliance objectives in the cloud.
Image licensed by: Unsplash.com
Related News: