The compromise of one cell phone could be a true existential challenge for many organizations today. Think about the damage an adversary could do if they got ahold of a phone that belongs to an IT pro with privileged access to your key systems or to an employee who works with financial records or other sensitive data.
This article will help you tighten the security of your phone, benefitting both your organization and your personal life. This article is iOS centric because I personally use an iPhone, but similar strategies can be applied in the Android world.
I will cover three types of protection:
- Protection against physical theft of your iPhone
- Protection against SIM swapping attacks
- Extra protection for users with access to sensitive data and systems
Protection against physical theft
Unless you take some simple precautions ahead of time, having someone steal your iOS device can be a real disaster. Indeed, if they also watched you type in your password, they can essentially BECOME you. They gain access to a treasure trove of your personal information, perhaps including your Social Security number and pictures of your passport. Plus, they can use Apple Pay to run up bills using your credit cards.
Worst of all, they can change your Apple password and take over your whole Apple ecosystem. Let me say that again: Knowing your iPhone (or iPad) unlock code is the gateway to an adversary taking over your whole Apple identity.
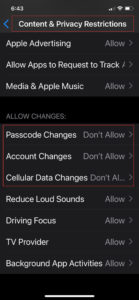
Fortunately, you can take steps now to prevent this from happening. Go to Screen time and enable Content & Privacy Restrictions. Then disable changes to Passcode, Account, and Cellular Data, as shown here:
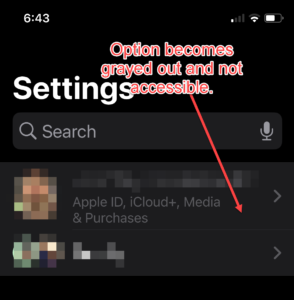
Then you’ll need to set up a second 4-digit passcode that will be required to turn Screentime / Content & Privacy off or back on. Then, even if someone has your iPhone and your main unlock passcode, it will be impossible for them to change your Apple ID or password. As you can see below, Apple ID, iCloud+, Media & Purchases becomes unclickable:
Note that you need to do this for each iOS device you have; doing it once doesn’t magically replicate the setting across all your iOS devices.
This strategy is quite useful, but it has an important limitation: An adversary who has your phone and passcode will still be able to access all the credentials stored in your Apple iCloud Keychain, so they can log in to your online banking and other website accounts and create all kinds of havoc.
Therefore, I strongly recommend using a non-Apple password manager rather than Apple Keychain, to store your credentials. To turn off Apple iCloud Keychain follow the instructions here: https://www.howtogeek.com/718499/how-to-disable-icloud-keychain-on-iphone-and-ipad/. And here’s how to transition to Bitwarden, a popular password manager: https://www.howtogeek.com/715490/bitwarden-is-the-best-free-alternative-to-lastpass/
Protection against SIM swapping
Organizations often use multifactor authentication (MFA) to provide additional protection for sensitive data and systems. It’s important to use non-SMS methods, such as Okta or Azure AD MFA, to secure all privileged systems.
That’s because MFA via SMS is risky. Of course, if your iPhone is stolen, an adversary can get the SMS codes sent to it. But even without having your iPhone physically in hand, they can access your SMS codes by using a SIM swapping attack — they convince your cell phone carrier that they are you, and claim that you’ve lost your cell phone and need a replacement SIM card. Each mobile phone carrier handles this situation a little differently; this article provides more details.
The key defensive action you can (and should) take is to call your cell carrier now and add enhanced protection (typically, a long extra pin code) that you must provide to their agent in order to make any account changes. Therefore, whenever possible, don’t get MFA codes by SMS; use app-based MFA instead. This is a time-based code (typically 30 seconds) where a code rotates and you put that in as your second factor. There are a number of options, including Google Authenticator or Microsoft Authenticator. I recommend the free Authy app by Twillio. It enables you to share entries across multiple devices, so if your phone gets dropped in a lake (or, more likely, a toilet), it’s easy to keep working using another one of your devices. You can also require a separate PIN or Face ID to open the Authy app, which I strongly recommend. That way, if bad a guy gets your physical phone and knows the code to unlock it, they cannot unlock Authy.
Extra protection for users with access to sensitive IT assets
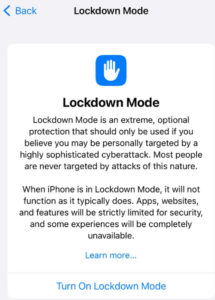
Even if you’re not an IT admin with privileged access, you might be on a team that deals with finances or is privy to other sensitive information. In that case, I recommend you enable iOS Lockdown Mode.
First, let me bust a common myth: iOS Lockdown mode isn’t nearly as scary as it sounds. The Lockdown Mode screen shown below has a lot of warnings, but I assure you, it isn’t difficult at all, and it’s also completely reversible.
Lockdown Mode blocks many kinds of inbound communication that could trick you into turning over the keys to your castle to the bad guys. Here are the main things that Lockdown Mode does:
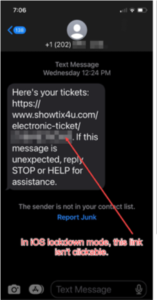
- It prevents links in SMS texts from being directly clicked upon; you can copy and paste them into a different app, which may allow clicking on them. (Note this restriction applies only to SMS and iMessages; it doesn’t apply to chat apps like Facebook Messenger or WhatsApp.) This is vital because if you’re like me, you get all sorts of “click here” SMS texts like this one:
- Lockdown Mode blocks hard-wired connections to computers to protect against “juice jacking.” This attack often takes place at airports and other places with free power; the bad guys can hijack your phone as soon as you plug it into their outlet, as shown in this short video.
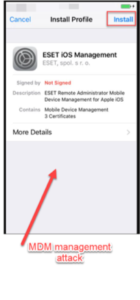
- Lockdown Mode will also block your phone from enrolling in a mobile device management (MDM) provider. This will block SMS requests from bad guys attempting to enroll your device in their MDM service in order to own your device, as shown here:
In fact, I recommend that everyone at your organization, regardless of their role, turn on Lockdown Mode and try it for a week. If you hate it, you can simply turn it back off.
I’ve been using Lockdown Mode ever since it was released and I have had literally zero problems. True, not being able to click on links from your Aunt Sally to view cat-related YouTube videos is a little bit of a bummer, but that’s a small price to pay for increased security for yourself and for the whole company.
Final thoughts
The goal isn’t security perfection; it’s security improvement. If you act upon one or more of the suggestions in this article, then you’ve done more to protect your device than most people out there.
To learn more about Netwrix, visit the website HERE.
Related News:
2023 Gartner Magic Quadrant Has Recognized Netwrix a Visionary
Netwrix MSP Sector Report Finds Data and Network Security Top Priorities